- Author Matthew Elmers elmers@military-review.com.
- Public 2023-12-16 21:49.
- Last modified 2025-06-01 06:23.

Information is the most powerful catalyst for a collaborative approach to warfare, a so-called "system of systems"
Information propels information gathering, surveillance and reconnaissance (ISR), command and control (C2) and multifunctional information and control system (C4I), empowering all cooperating combat units and expanding their tactical boundaries of combat space. Networked tactical information systems provide information superiority, which allows the military to expand their situational awareness across the entire strategic spectrum of combat operations, make time-limited decisions based on aggregate multimedia and multispectral data in real time, accurately plan combat missions, conduct target designation and assess combat losses (all of which reinforce and maintain a critical pace of operations) and evaluate reliable distributed mobile communications at the theater of war (theater of operations) and below
In the words of Lt. Gen. Charles E. Groom, director of the Defense Intelligence Assistance Network (DISA) Joint Operations Directorate in Arlington, "Information is America's most formidable weapon."
"When information doesn't focus on action," develops Groom's thought, "then solutions don't work." Therefore, information is the most powerful catalyst for a system of systems (or global system) approach to warfare. It underpins network-centric combat operations, which are key to the successful implementation of transforming defense initiatives, including the global system's network-centric common combat space (SOSCOE).
Information flow is important
Similar to command, control and communications (C3) functions, combat automation, such as remote control of UAVs and other unmanned systems, relies on the timely and free flow of information for end users at all echelons, from fixed tactical operations centers (TOCs) to active and mobile forces. on the theater. Difficulties can arise where there are gaps in network coverage or loss of connectivity that create blind spots and reduce the efficiency, speed and reliability of network coverage, usually between headquarters and dispersed and forward forces such as field commanders and dismounted infantry. When troops on the move are denied access to the mobile network, in order to continue their combat missions, they often have to resort to narrow-band, low-resolution communications and solutions when they lose contact with tactical control centers.
Such gap avoidance measures could essentially shift end-users of information streams from the digital era to tactical solutions from the Vietnam War era in an instant, as soldiers are forced to default to printed cards instead of digital displays and to voice-based ordering in order to be able to communicate. radio instead of broadband multichannel systems that are available to command echelons with large resources of stationary network systems. Operational concepts like information superiority are of little value if they cannot be successfully applied across the entire strategic range of military operations, including operations in which often widely distributed troops below divisional level need access and use of coordinated and integrated tactical capabilities and functions within an overall framework of operational interconnectedness. …
To expand and deepen network-centric combat operations (SNOs), mobile warfare information equipment, tactical network communications and dismounted operational controls integrated with rapidly regulated, survivable and user-transparent global networks must conform to the soldier as a system philosophy. which is central to the doctrine and implementation of network-centric warfare. Networked services and information equipment allow personnel to conduct combat operations within an impact-based non-linear combat space, facilitate and facilitate the use of transformational network-centric military strategy, and enable combat operations across the entire range of common digital combat.
Colin Bubb, a spokesman for the Office of Naval Research (ONR) public relations office, said the strategic plan, presented by the Marine Corps Warfighting Laboratory (MCWL), is for mobile information systems to deploy operations with armed forces at different levels in an asymmetric combat space. The MCWL plan is one such initiative, both in the US and around the world, as the military strives to become fully network-centric in its operations and these initiatives continue to use inherent information architectures. Key concepts were tested during a military exercise like the JEFEX 2012 (Joint Expeditionary Force Experiment), which was completed in April 2012 and focused on cooperation and communications across strategic, operational and tactical spectrum in order to plan and execute global combat operations based on information. The recent MNIOE (Multinational Information Operations Experiment) exercise by 20 EU partners led by the German Ministry of Defense also confirmed the effectiveness of network-centric information operations in a joint multinational combined arms space. In addition, Operation Iraqi Freedom itself confirmed for the SBO designers the correctness of the regional test model, the correct path of military development since the era of the first Gulf War, along which the Americans and their partners in the multinational coalition traveled.

IRobot Game Boy style controller and PCC laptop

Expeditionary 31 data scientist configures SWAN satellite system during communications exercise at Camp Hansen
The role of information technology
While information superiority is a key driver, information equipment is needed to facilitate governance, connectivity, service integration and data management, coalition accessibility, key information products, service discovery, information discovery, and data visibility. Indeed, a constellation of mobile, networked information equipment, scalable architecture, and high-level services are required to expand the Global Information Coordinate Network (GIG) right into the hands of the soldiers in the battlefield who define tactical boundaries on a daily basis.
Backbone services are at the heart of all network connectivity. Backbone services can be said to include the totality of all network interconnectivity, which can be defined in various ways as a "network" or "mesh" for communication lines and bandwidth. Regardless of how, where, or in what context they are used, backbone services form integral and fundamental combat awareness and impact-based military operations, enabling combat support from a combat unit's perspective and providing the means for accurate real-time behavior. The network processes that enable backbone services range from laptop-to-laptop operations such as secure email, intranet and tactical Web 2.0 services, to complex C4ISR operations (command, control, communications, computers, collection information, surveillance and reconnaissance), for example, those that are consistent with the management of strategic UAVs like GLOBAL HAWK.
Integral with respect to dynamic network-centric operations for mobile troops are special networks (MANET). These are scalable, adaptable, broadband networks conforming to common operational standard protocols that provide a tactical broadband backbone for reliable, distributed C2 (operational control), C4 (command, control, communications and computing), C4I and C4ISR operations of all types. Such networks can be of different shapes and based on different system architectures and deployed topologies. Wireless mesh networks, for example, consist of transmitting nodes organized in a mesh topology (a network topology in which there are two (or more) routes to any node) that does not rely on fixed or static terminals, but can use information equipment such as combat radio stations, individual nodes, forming networks on a specialized basis. The coverage area of radio nodes operating as a single network is sometimes referred to as a "mesh cloud". Access to this "mesh cloud" depends on radio nodes operating in sync with each other to create a dynamic radio network. Redundancy and reliability are key elements of such networks. When any single node is no longer operational, functional nodes can still communicate with each other, directly or through intermediate nodes. Such dynamic, self-forming networks are also described as self-healing.
The Wireless Adaptive Network Development (WAND) program is currently using mesh principles in a project aimed at producing tactical radios using commercial components that are self-adapting to the electronic space in which they are deployed, automatically switching frequencies and bypassing jamming and improving network performance in a wide range of tasks. MOSAIC (Multifunctional On-the-Move Secure Adaptive Integrated Communications) is conceived as an initiative to demonstrate a multifunctional mobile adaptable radio network based on web 2.0, Internet protocols supporting wireless access, which can be connected to terrestrial and satellite networks for global connectivity. with a high degree of information security guarantee due to built-in programmable encryption and self-healing characteristics. WIN-T (Warfighter Information Network -Tactical) is a high-speed wireless tactical network architecture based on web 2.0 implementation and a transitional concept to develop Wireless Network After Next (WNaN) architectures that will be combined with radios with XG technology (Next Generation), for example, developed according to the standards of the JTRS program (Joint Tactical Radio System Network - reprogrammable radio stations using a single communication architecture), based on a programmable, multi-transceiver architecture,which will allow them to quickly adapt and reconfigure as operational conditions change, including jamming, eavesdropping and hacker attacks.

Network servers for the global computer network (division level)
Development of protocols
Protocols for tactical networks are many and constantly evolving:
C2OTM (Command-and-Control On the Move). Dynamic protocols use SIPRNet (Secret Internet Protocol Router Network) and NIPRNet (Non-Secure Internet Protocol Router Network), US Department of Defense broadband Internet, and mobile connectivity.
DAMA (Demand Accessed Multiple Access) networks. These standards are used in flexible, user-configurable satellite terminals that carry data and voice.
FBCB2 (Force XXI Battle Command Brigade and Below - a 21st century control system of the brigade level and below). Standards for performing dynamic combat control of a mobile tactical network.
JAUS (Joint Architecture for Unmanned Systems). It is a generic operating system protocol for performing combat robotic operations within the concept of a global system.
JTRS (Joint Tactical Radio System - a network based on reprogrammable radio stations using a single communication architecture). The evolving mesh ad hoc network communication protocol defines a new class of military radio transceivers (transceivers).
MBCOTM (Mounted Battle Command On The Move). Facilitates data reception and transmission for SINCGARS (Single Channel Ground and Airborne Radio System) devices in BRADLEY and SRYKER combat vehicles, helping to increase situational awareness on top of the existing Army Combat Command System (ABCS).
MOSAIC (Multifunctional On the Move Secure Adaptive Integrated Communications). Another dynamic, mobile networking standard.
NCES (Net-Centric Enterprise Services). Unit-level Web 2.0-based network services for the US Department of Defense, developed by DISA (Defense Information Systems Agency, the structure in the US Department of Defense responsible for the implementation of computer technology).
TACSAT. The protocols utilize a tactical satellite communications network, the Joint Warfighting Space (JWS) orbital initiative, also known as the Roadrunner, with built-in intelligence support for combatants during network-centric combat.
WIN-T (Warfighter Information Network -Tactical - army tactical communication system). High-speed, broadband network protocols for the US Army's mobile communications.
VOIP (Voice Over Internet Protocols). This known technology involving enterprise data transmission in a commercial domain has also been modified for use in military cellular and broadband communications networks.
All of these protocols support soldier-as-a-system integration policies, networking between vehicle electronics, and interface to high-level architectures such as satellites, strategic drones, and combat robots. In addition, all use open operating standards and layered architectures, which allows systems to be modernized rather than "remodeled" by adding or detaching layers of a system based on the implementation of advanced technologies.
The interconnectedness provided confirms the fact that information is the most important enabler for the system of systems (global system) principle, which includes the creation of a network in the combat space, customizable, scalable networks that include friend or foe technology and keep the soldier in communication with other soldiers … This factor acts to support systems, including robots, throughout the combat space.
However, even if information superiority is the key to dominance strategy, information has no value without data processing equipment, prioritization and distribution to end users in theaters and in remote areas. Therefore, there are numerous initiatives in prototyping, field evaluation and production of such equipment.

A systems engineer from Northrop Grumman shows the connection to a combat network using Soldier Ensemble, which includes a small computer.
System overview
Just as a tactical network must offer high transparency and scalability for the user from the side of services, devices that will allow information exchange between people must offer transparent, soldier-friendly interoperability, high degrees of compactness, ultimate reliability, survivability and mobility in a combat space. The end users of such systems will be distributed across all combat echelons from mobile tactical command centers to dismounted infantry. One of the main goals of system designers for tactical information equipment, such as combat laptop computers, is how easily these systems will align with the right soldier who has grown up in a common culture today and is literally immersed in information technology at every level. Consequently, the starting point for many, if not all, products were originally developed at the enterprise level for commercial use and modified with firmware and software upgrades consistent with military applications and packaged in special ruggedized "foolproof" cases., and meeting military standards, such as MIL-STD-810E of the US Department of Defense. For example, these include Panasonic's Toughbook laptop and the Paq Compaq PDA handheld computer, both used extensively by coalition forces in Iraq and Afghanistan. A hardened version of the latter is known as RPDA or CDA (Commanders' Digital Assistants). Recently, hardened tablets for military and paramilitary forces have become widespread.
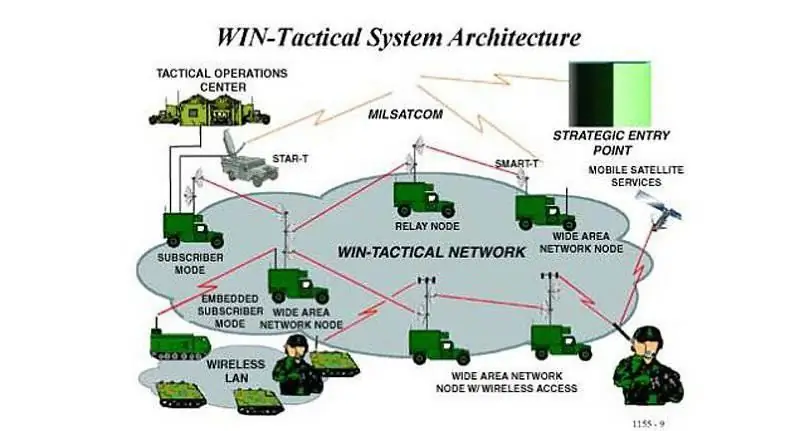
WIN-T (Warfighter Information Network-Tactical) network architecture

The special operations force commander calls the operations center to report the location of his group

A WIN-Tactical Phase II vehicle awaits driving instructions during a WIN-T technology demonstration at Navy Air Base Lakehurst

Tactical Network Management Console from Canadian Signals
Other off-the-shelf joypad-like hand controllers, including GameBoy and Sony PlayStation controllers with joysticks and push buttons, have been modified for military use, especially for remote control of combat robots, such as iRobot's PACKBOT and the SUGV variant of the small ground vehicle found on armament of the American army. This is the case with WiiMote controllers, originally developed for the Wii game consoles and the Apple iPhone cell phone, both with Wi-Fi wireless connectivity. In the case of the iPhone, control devices based on reconfigured iPhone and iPhone-type Wi-Fi platforms have been refined to control the PACKBOT robot and the larger ground vehicle CRUSHER, developed by the Robotics Institute of Carnegie Mellon University as part of the DARPA technology initiative. (Office of Advanced Research and Development, US Department of Defense). Among such devices is the JAUS-compatible universal robot control device SURC (Soldier Universal Robot Control), which was developed by the Applied Perception Corporation for the research laboratory of the American army.
Even with fully proprietary, specialized control units designed for military applications, such as the Wireless PCC (Portable Command Controller) for the PACKBOT 510, a familiar user interface defines the system configuration. He and similar controllers (control devices) for other military robots, including DRAGON RUNNER and SWORDS, have a similar design, laptop, LCD or plasma flat panel displays, keyboards that are not afraid of spilling liquids and joypad control handles. An example is a special DCU (Direct Control Unit) for telecontrol of the TALON-3 SWORDS robot, which was deployed in Iraq and Afghanistan.
Wearable information devices can free up hands for operational control applications and also serve as useful situational awareness tools for the soldier as a system. These devices are based on wearable displays, whose user interface is semi-immersive (immersive - creating the effect of presence), “transparent” virtual space, in which tactile control mechanisms can also be used, such as exoskeletons for hands and fingers instead of pointing devices such as mice and input devices type of keyboard.
The preferred user interface is a binocular or monocular head mounted display (HMD). These displays are usually conventional OLED micro-displays (organic light-emitting diodes) and are very lightweight, especially when compared to older designs. These devices use standards and protocols that are consistent with soldier-as-a-system concepts, such as the Future Force Warrior (FFW) WACT helmet-mounted display subroutine. Typical systems developed are Liteye 450 from Liteye Corporation, ProView S035 HMD and Thermite Wearable PC from Rockwell Collins Optronics. Other systems include the Virtralis system manufactured by Polhemus Corporation in California. The Virtralis, which uses an OLED microdisplay and a tactile wrist control exoskeleton (similar to the Cyberforce tactile hand controller from Polhemus Corporation), is currently being evaluated by the British Air Force.
In addition to dismounted command and control applications such as ground, air, and naval robotic systems, tactical information devices play important roles in all soldier as a system combat initiatives related to anywhere connectivity issues affecting effective layered combat coordination. combat space. Systems to support mobile operational control applications such as the FBCB2 program include portable, highly reliable C4 (Command, Control, Communications and Computers) systems such as TWISTER, which can be turned into mobile control centers with reliable broadband links and provide tactical TVD networks such as satellite communication and information transmission network Trojan SPIRIT (Special Purpose Integrated Remote Intelligence Terminal - special remote data collection terminal).

The picture shows the on-board automated data transmission terminal M-DACT (Mounted Data Automated Communications Terminal). It is a combat portable computer that connects to a location-based transmission system to receive wireless Internet, and also works as a high-precision GPS receiver. Through the M-DACT wireless Internet, he can access a network with a secure Internet protocol in order to establish communication with other departments
Vehicle-mounted C4 systems use handheld computer terminals, sometimes called "add-on" terminals, that can be installed on combat vehicles for mobile network communications, data exchange, targeting, and other network-centric information operations. An example of the transportable terminal system deployed by the US Army in Iraq and Afghanistan and the standard interface for the transportable FBCB2 system is DRS Technologies' robust transportable RVS 3300 system, which is fully compliant with the MIL-STD-810E standard for optimal interaction with the mobile tactical end user. … It includes a sealed membrane keyboard, anti-reflective, high-resolution LCD touchscreen display, wireless integration with existing tactical networks, and built-in standards support for communication and installation in a vehicle. Other systems suitable for these tasks and usually installed in vehicles include the already mentioned Toughbook in a transportable configuration and the reliable rugged SCORPION RVT terminal, used in tandem with PPPU (Platform Digitization Processor Unit), a processor for mobile applications that meet military standards and allow for operation in extreme conditions.
Estimates and projections
As combat space networking becomes the model for network-centric operations, applications for them will continue to evolve. This development is assured as information will continue to serve as a critical agent for successful warfare in the 21st century. Even a cursory examination of the budgetary allocations of the Joint Department of Defense Headquarters in 2009-2013 shows that the constantly growing allocations for important components of all types for waging network-centric warfare and initiatives to transform American defense, such as the Future Years Defense Plan (defense plan for future years), confirmed that armed forces will become increasingly information-based and will be equipped with various highly intelligent robotic systems (land, air, sea) by the end of the second decade of the 21st century. Over time, all military operations will become mostly information operations!
While specifications and requirements have evolved and will continue to evolve, the core service components have been well defined over the past several decades. Improvements and upgrades will continue, but the core components of any reliable military network, such as connectivity and bandwidth, information reliability, and scalability and flexibility, will remain well-known elements built into both future and existing systems. There needs to be a consistent use of off-the-shelf elements and layered architecture in the future, as is the case today.

The global logistics support network LSWAN (Logistics Support Wide Area Network) makes it possible to install a wireless network in a TVD and create an insecure Internet router (NIPR), a secure Internet router (SIPR), or work in conjunction with other logistics systems

DTAS (Deployed Theater Accountability Software) abbreviation software for personnel and contractors

Signals on their knees writing advance directives during the annual NCO competition

WIN-T is a military tactical telecommunications system for the 21st century, consisting of infrastructure and networking components from the battalion level to the theater of operations. The WIN-T network provides C4ISR (Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance) capabilities that are mobile, secure, highly survivable, seamless and are capable of supporting multimedia tactical information systems.
The ability of the network to support the reorganization of unit tasks and change tasks in real time is a vital mover of the army's operational concepts. The WIN-T network allows all army commanders and other users of the communications network at all echelons to exchange information inside and outside the theater of operations using wired or cordless phones, computers (similar to the Internet) or video terminals. Soldiers and communications units deploy their standard WIN-T systems to integrate global and local war networks into a commercial IT-based tactical network
Information assurance issues will continue to pose challenges as the capabilities and complexity of systems develop and become more distributed across the global information network, since the increasing proliferation of systems and architectures that support network-centric operations means increased risks of sabotage, including attacks on services, the spread of malware, and others. forms of information attacks. This is especially true as the trend continues in military systems to use Web technologies like their predecessors. This increases the risk of being exposed to threats similar to those that constantly plague systems designed for the private sector.
In short, increasing use and increased complexity add to the increasing challenges of improving security. Technologies such as built-in device encryption, IT-based security policies, and remote blocking are currently proposed countermeasures that promise to reduce the likelihood of threats, but security measures for evolving future systems will require much more proactive risk management than this. is declared for the current generation of tactical networked systems architecture, and, in addition, even more attention may be needed to the immediate successors of such systems.
As you can see from the above, there is an increasing need to provide better and more comprehensive integration with robots in the combat space. Realizing the concept of soldier as a system requires robotization of about a third of the US military by 2020. The transformation of the robotization process portends not only more than just an increase in the number of robots in the combat space or an increase in their presence; it also heralds an increase in the number of tasks across the growing spectrum of conflicts. All this creates much higher requirements in comparison with the current ones. This extraordinary increase in throughput will require tomorrow's mobile tactical information systems and broadband networks to be much faster, much more intelligent and dynamically reconfigurable than existing ones, including the evolving WNAN.
It can be assumed that the trend of transfer of technologies developed by the commercial sector to the defense sector may be supplanted by the development of parallel systems for the whole defense sector in order to meet emerging tasks, although this is by no means defined.
The future fusion of friend-or-foe technology is another area where new systems can help dispel the long-standing fog of war and solve problems that have not been solved in the past.
Finally, there were some imbalances between the vision of the planned and the current critical milestones achieved in the development of next generation tactical networking technologies, as well as critical issues of interoperability and interconnectivity within the army. These problems lead to interference in getting services and systems into the hands of the military in a war zone, an example is the implementation of extensions to the IEEE 802.11v (Wi-Fi) standard of the coalition forces, which is compatible with wireless mesh networks. Another such example is JTRS-compatible radios with built-in MANET compatibility.
Several communications interoperability issues remain unresolved due to the use of a wide range of operating frequencies, which overwhelms the specialized verified services organized by the coalition partners. This sometimes forces some of the system's functions to be handed over to civilian cellular operators, as was the case with leading Iraqi cellular provider Zain, which was used by both civilians and the military, thanks to the well-known high reliability of this commercial network. Despite these and similar growing problems, networked tactical information systems have already fundamentally changed combat operations, bringing the doctrine of transformation to the forefront of tactical warfare, and adding energy to combined arms and special combat operations. As Shakespeare once wrote in his play The Tempest: “The past is just a prologue. The rest is usually history."






